Email remains the primary channel for communication, collaboration, and commerce. However, this ubiquity also makes it the number one attack vector for cybercriminals. Email security solutions are no longer just about filtering out annoying spam; they are sophisticated, multi-layered defense systems designed to protect organizations from a barrage of advanced cyber threats. These comprehensive platforms leverage cutting-edge technologies like artificial intelligence (AI), behavioral analytics, and real-time threat intelligence to defend against devastating attacks such as phishing, Business Email Compromise (BEC), ransomware, and other malicious email-borne campaigns.
Quick Answer: Email Security Solutions Comparison
| Architecture Type | Best For | Key Advantage |
|---|---|---|
| API-Based Solutions | Businesses using cloud email platforms like Office 365 and Google Workspace. | Offers real-time, post-delivery scanning and remediation without disrupting mail flow. Catches internal threats. |
| Secure Email Gateway (SEG) | Organizations with on-premises or complex hybrid email environments. | Provides granular, pre-delivery control over all incoming and outgoing mail flow. |
| Integrated Cloud Email Security | Organizations seeking the deepest level of protection within their cloud suite. | Continuously monitors the cloud environment for threats, offering post-delivery remediation and account takeover protection. |
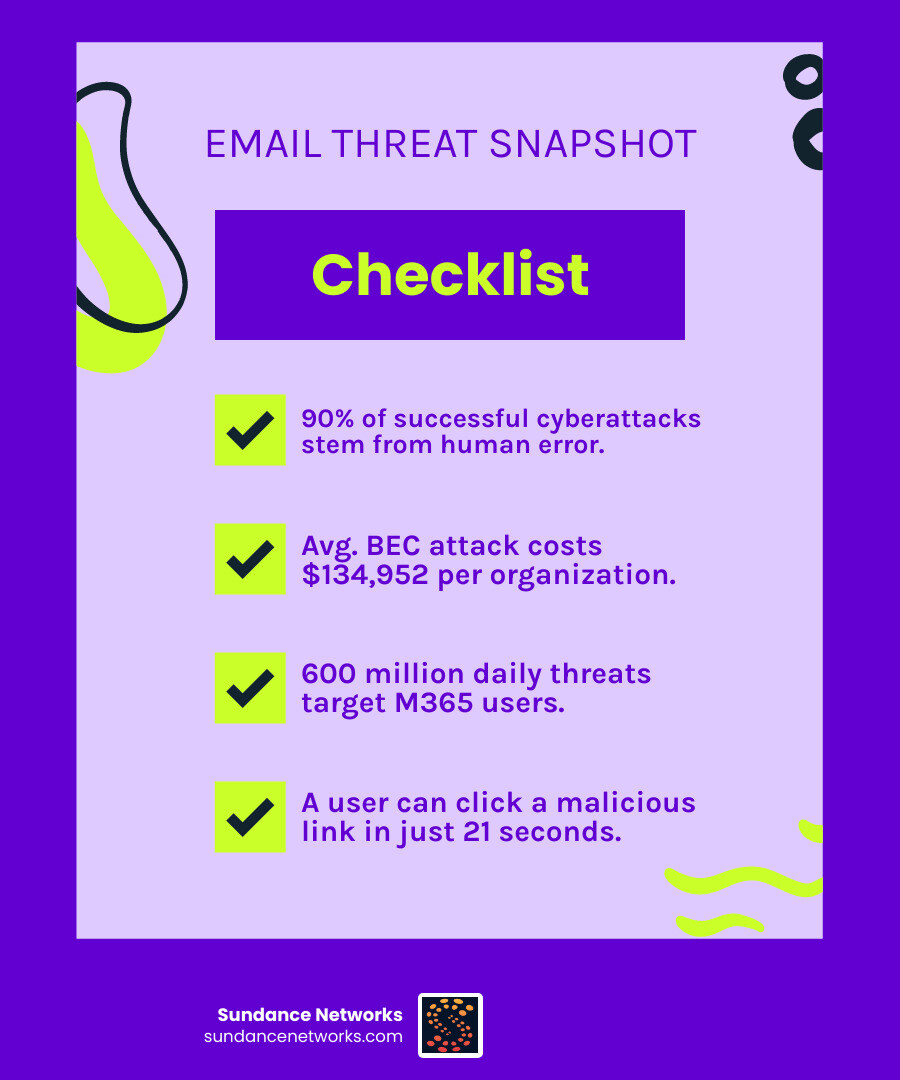
The stakes have never been higher. Research consistently shows that more than 90% of successful cyberattacks are rooted in attacks targeting people and human error, with email being the primary delivery mechanism. The financial and reputational damage can be catastrophic. The average cost of a single Business Email Compromise attack now exceeds $134,952 per organization, while Microsoft 365 customers alone face an astonishing 600 million threats every day.
Today’s cybercriminals have moved far beyond simple, generic spam campaigns. They are weaponizing generative AI to craft hyper-personalized, context-aware attacks that can deceive even the most security-conscious employees. These threats include highly sophisticated phishing schemes, CEO fraud, vendor impersonation, account takeovers, and emerging tactics like QR code phishing (quishing) and Telephone-Oriented Attack Delivery (TOAD).
The challenge is clear and immediate: it takes just 21 seconds for one user to click a malicious link, potentially compromising an entire network. Traditional email security approaches, which rely heavily on signature-based detection and basic spam filters, are fundamentally incapable of keeping pace with the speed, volume, and sophistication of these modern threats.
Modern email security solutions address this gap by implementing multiple, overlapping layers of protection. They combine AI-powered behavioral analysis, real-time threat intelligence feeds, advanced sandboxing for attachments and links, and automated remediation capabilities to identify and neutralize both known and unknown threats before they can cause harm.
The Modern Threat Landscape: Why Standard Inboxes Aren’t Enough
Remember the good old days when an email threat was just a cheesy spam message about a faraway prince? Ah, simpler times! Today, things are a little more… intense. Our inboxes have become prime targets for cybercriminals who are crafty, persistent, and always evolving. They know that email is the heart of most business communication, making it a golden opportunity for them. That’s why top-notch email security solutions aren’t just a nice-to-have anymore; they’re an absolute must for any organization that takes its security seriously.
Let’s explore some of the tricky email threats floating around. You’ve probably heard of phishing, where sneaky emails pretend to be from a trustworthy source—like a bank, a software vendor, or even your own IT department—to trick you into clicking a malicious link or sharing your login credentials. It’s an old trick, but it remains incredibly effective because it preys on human psychology.
Then there’s the highly damaging Business Email Compromise (BEC), sometimes called “CEO fraud.” This is where attackers use social engineering and impersonation to mimic a high-ranking executive or a trusted vendor. They might send an urgent email to the finance department requesting a wire transfer to a fraudulent account. As CISA explains, these attacks are difficult to detect because they often don’t contain malicious links or attachments, relying instead on deception. A single successful BEC attack can cost a business an average of $134,952 – a potentially devastating financial blow.
But the bad guys don’t stop there. They also use email as the primary delivery vehicle for ransomware, which can encrypt all your critical data and hold it hostage until you pay a hefty ransom. They also distribute plain old malware like viruses, spyware, and keyloggers designed to disrupt your systems or steal your trade secrets. And watch out for impersonation attacks, where criminals mimic anyone from a colleague to IT support just to gain your trust and extract sensitive information.
They’re even getting creative with new tactics like Telephone-Oriented Attack Delivery (TOAD), where an email’s goal is to get you on the phone with a scammer, completely bypassing traditional email filters. And have you heard of QR code phishing (or “quishing”)? Attackers embed malicious links in QR codes within emails, turning a convenient scan into a major security risk. It’s wild out there!
These threats are constantly shifting and adapting, which is why strong Cyber Security measures are so important. After all, when Microsoft 365 users alone face an astounding 600 million threats every single day, you know you need more than just hope on your side. This isn’t just about blocking spam; it’s about building a resilient defense against the next generation of email attacks.
The Rise of AI-Generated Threats
Now, let’s talk about the game-changer: generative AI. This technology has thrown a massive curveball into the cybersecurity world. What used to take a skilled criminal hours to craft – a grammatically perfect, contextually aware, and highly convincing fake email – can now be generated automatically, at scale, and at lightning speed! This means the barrier to entry for cybercriminals has been significantly lowered. Even less tech-savvy bad actors can now launch incredibly persuasive and hyper-personalized attacks.
Imagine getting an email that perfectly mimics your CEO’s writing style, references a recent internal project, and urgently asks for a wire transfer to a new vendor. Sounds familiar, right? But now, AI makes these scams shockingly real by analyzing public data and previous communications. These AI-powered attacks move at machine speed, making them nearly impossible to spot with manual review. They’re so personalized that they can easily trick even the most vigilant employees, leading to sophisticated social engineering. Furthermore, they can adapt on their own, creating more frequent and novel zero-day threats – attacks that exploit brand new vulnerabilities before anyone even knows they exist. It’s like social engineering on steroids!
It’s a bit like a digital arms race, isn’t it? The ‘bad AI’ out there means we absolutely need ‘good AI’ working hard on our side to defend against these advanced threats.
The Limitations of Built-In Email Security
Now, you might be thinking, ‘But wait, my cloud email platform, like Microsoft 365 or Google Workspace, has built-in security, right?’ And you’d be correct! These platforms offer a solid foundational layer of defense, and they’re constantly improving. However, when it comes to truly sophisticated, AI-powered, and socially engineered threats, those built-in features often aren’t quite enough.
The truth is, there are some pretty big gaps in default protection. While your everyday spam and known viruses might get caught, the really clever stuff—payload-less BEC attacks, zero-day threats, and highly targeted spear-phishing emails designed to mimic legitimate communications—often sails right through. In fact, some industry reports show that as much as 47% of threats that advanced, specialized email security solutions catch are actually missed by the native tools in platforms like Microsoft 365. That’s nearly half of the most dangerous attacks reaching your employees’ inboxes!
It’s not that these platforms are bad – they’re excellent for productivity and basic filtering. But they are built for a massive, general audience and may not have the super-specific, deep-dive behavioral analysis needed to spot the trickiest attacks. Think of it like this: your office building has a lock on the front door, but you still have locks on individual office doors and safes for your most valuable assets. Relying only on built-in email security is like leaving the safe wide open.
This is why there’s an undeniable need for layered security. We simply have to augment those foundational defenses with advanced, specialized email security solutions. These solutions are specifically designed to catch the threats that sneak past the first line of defense. The real value? They protect your most vital communication channel by catching what others miss, giving you comprehensive peace of mind and a resilient security posture.
Architectural Approaches: How Email Security Solutions Work
When it comes to securing our email, not all solutions are built the same. The architecture of a security solution determines how it integrates with your email system, how it inspects messages, and what kinds of threats it is best equipped to handle. Understanding the underlying architectural approaches is key to choosing the right fit for your organization. Broadly, we can categorize modern solutions into two main types: traditional Secure Email Gateways (SEGs) and modern API-based solutions.
SEGs act as a checkpoint, sitting in front of your email server. To implement a SEG, you must change your domain’s MX records to reroute all incoming and outgoing email through the gateway for inspection before it reaches your mail server. API-based solutions, on the other hand, integrate directly with cloud email platforms like Microsoft 365 and Google Workspace via APIs, allowing them to scan emails after they have been delivered, providing continuous monitoring and remediation within the inbox itself.
Comparing Email Security Architectures
Let’s break down the key differences in a direct comparison:
| Feature | Traditional Secure Email Gateway (SEG) | Modern API-Based Solution |
|---|---|---|
| Deployment | Requires rerouting mail flow by changing MX records. Can be complex and cause downtime if misconfigured. | Deploys in minutes via API integration with cloud email provider. No change to mail flow. |
| Visibility | Only sees external email traffic that passes through the gateway. Blind to internal, east-west threats. | Has full visibility into all emails, including internal messages between employees and historical emails. |
| Threat Detection | Scans emails before delivery. Strong at blocking known threats, spam, and malware based on signatures and reputation. | Scans emails post-delivery and continuously. Uses AI and behavioral analysis to detect advanced threats like BEC and account takeover. |
| Remediation | Can block, quarantine, or strip attachments from emails before they reach the inbox. | Can automatically retract malicious emails directly from user inboxes even after delivery (clawback). |
| User Experience | Can introduce email delivery delays. Legitimate emails may be caught in quarantine, requiring IT intervention. | Seamless and invisible to the end-user. No delivery delays. Can place contextual warning banners on suspicious emails. |
While SEGs have been the standard for decades, especially for on-premises environments, the shift to cloud email has highlighted their limitations. Their inability to see internal-to-internal emails is a significant blind spot, as compromised accounts are often used to launch attacks from within the organization. Furthermore, the reliance on pre-delivery scanning means they can miss sophisticated, payload-less attacks that rely on social engineering rather than malicious attachments.








