How cybersecurity consultants use ai is changing the security landscape faster than ever before. Here’s the quick answer:
Primary Ways Cybersecurity Consultants Use AI:
- Real-time threat detection – AI analyzes network traffic and user behavior to spot threats instantly
- Automated incident response – AI systems isolate compromised systems and block attacks without human intervention
- Predictive threat intelligence – AI forecasts potential vulnerabilities and attack vectors before they’re exploited
- Improved attack path analysis – AI maps how attackers could move through systems and prioritizes defenses
- Streamlined compliance monitoring – AI automates security audits and regulatory reporting
- Intelligent vulnerability management – AI prioritizes which security gaps pose the greatest risk
The numbers tell the story. 64% of organizations now use AI for threat detection, while AI-driven systems blocked approximately 80 million fraudulent transactions in 2023 alone. Companies using AI-generated phishing training saw a 60% drop in click-through rates on malicious emails.
This shift is remarkable because consultants are using AI to fundamentally change security, moving from reactive fixes to proactive prevention. Traditional methods can’t handle today’s threat volume. AI processes data at machine speed, analyzing millions of events to find threats humans would miss. It’s like a security expert that never sleeps, gets tired, or misses a thing.
I’m Ryan Miller, founder of Sundance Networks. With over 17 years in IT and 10+ in information security, I’ve seen how AI delivers previously impossible protection. Implementing these solutions has shown me that AI isn’t just an improvement—it’s redefining what’s possible in threat prevention and response.
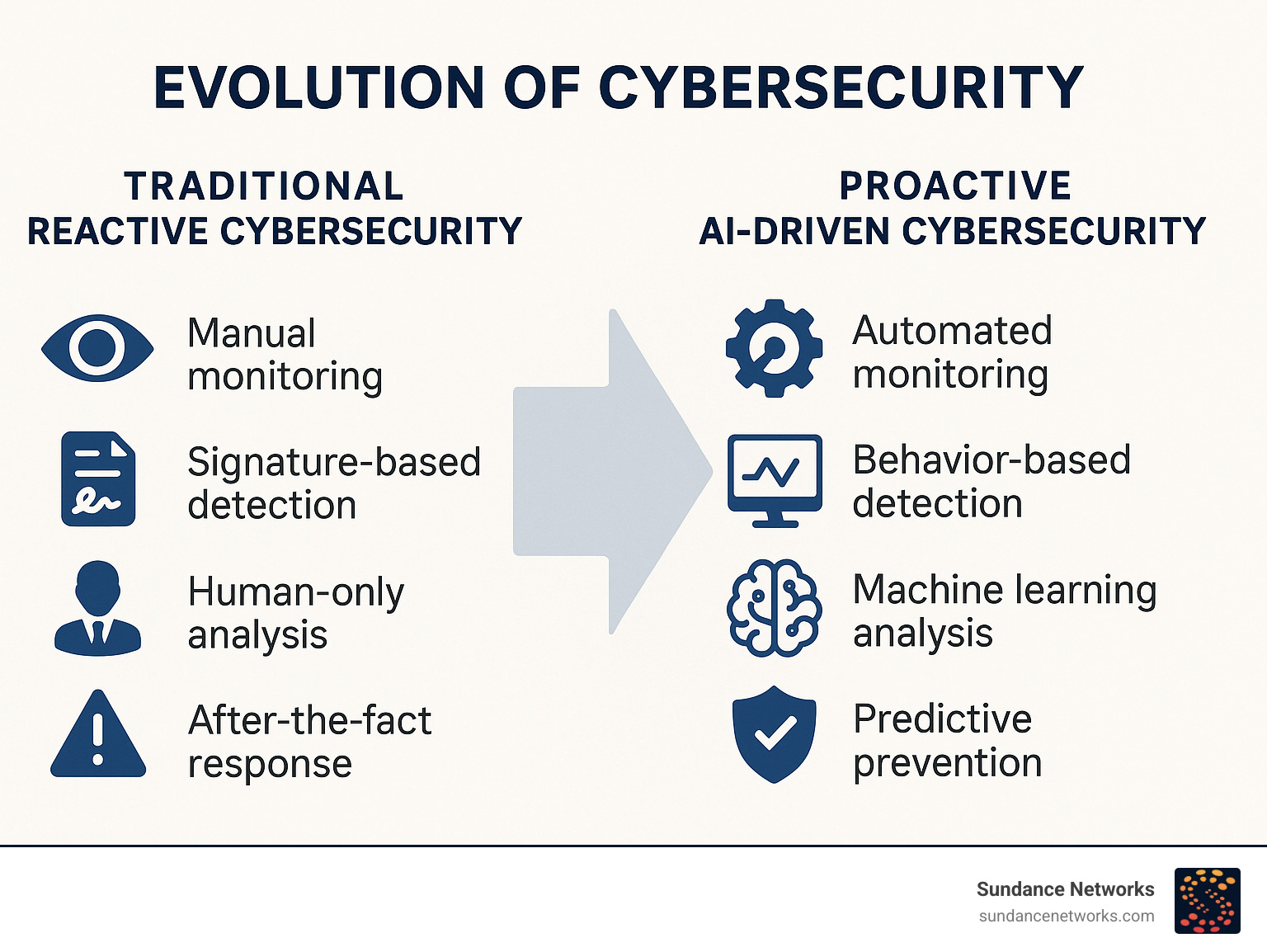
The New Playbook: How AI is Integrated into Modern Cybersecurity Strategies
Picture this: your security team is drowning in alerts while sophisticated attackers slip through unnoticed. This scenario is why how cybersecurity consultants use AI separates outdated security from effective protection.
Modern cybersecurity consultants are reshaping their strategies, making AI the central nervous system of intelligent defense operations. The shift is happening at scale. According to a CSA survey, 63% of security professionals believe in AI’s potential to improve security measures. This isn’t a trend—it’s a survival strategy.
What makes this change so powerful is AI’s role as a force multiplier. Instead of replacing human expertise, AI amplifies it. Consultants can now analyze data at an unprecedented scale, moving from reactive threat hunting to proactive defense orchestration. The result is a security strategy that anticipates attacks rather than just responding to them.
From Manual Defense to Automated Resilience
Security teams face an overwhelming reality: networks generate massive data volumes daily. Human expertise alone can’t process this information fast enough to catch sophisticated threats.
This is where AI augmentation transforms everything. Consultants use AI for heavy data analysis, pattern recognition, and initial threat assessment. It doesn’t replace human judgment but improves it by filtering noise and highlighting real threats for expert review.
The scalability benefits are remarkable. AI-powered systems can monitor thousands of endpoints simultaneously, correlating events across multiple data sources in real-time. This provides continuous, intelligent monitoring while human experts focus on strategic decision-making.
Crucially, AI dramatically reduces alert fatigue. By intelligently filtering and prioritizing alerts, it ensures human experts only see notifications that genuinely require their attention, preventing critical threats from being missed.
Our comprehensive approach to AI-improved security combines automated monitoring with expert human oversight. Learn more about our Cybersecurity services and how we implement these intelligent defense strategies.
Building a Data-Driven Security Posture
Effective AI-powered cybersecurity turns raw data into actionable intelligence. Big data fuels these decisions, as organizations generate terabytes of security-relevant data daily.
Machine learning models excel at finding subtle patterns hidden within this data. Unlike traditional signature-based detection that only catches known threats, AI-powered pattern recognition identifies suspicious activities based on behavioral deviations, catching new attack methods.
Anomaly detection becomes incredibly sophisticated with AI. The system learns what “normal” looks like for each user, device, and network segment. When something deviates from these learned patterns—like a user accessing unusual files at odd hours—the AI flags it for investigation.
Continuous learning makes AI-driven security powerful. Every new threat, false positive, and successful detection becomes training data that improves the system’s accuracy. Your security posture strengthens and adapts automatically to new threats and environmental changes.
Proper implementation requires expertise in both AI and security operations. Our team specializes in designing these integrated solutions through our Custom IT Consulting and System Integration services.
Core AI Applications: How Cybersecurity Consultants Use AI to Fortify Defenses
When how cybersecurity consultants use AI moves from theory to practice, threat management transforms from a reactive chore into a strategic defense system. Instead of a security guard watching one door, AI watches every entry point simultaneously and spots anything out of the ordinary.
Enhancing Threat Detection and Response
Modern cyber threats move faster than humans can react, making AI essential for defense. Real-time threat detection powered by AI analyzes massive datasets at lightning speed, catching subtle changes in network traffic or user behavior that traditional tools miss.
A powerful application is User and Entity Behavior Analytics (UEBA), which learns normal user behavior. It flags anomalies, like unusual access times or data movement, immediately. This is crucial for spotting insider threats, which are difficult to detect with traditional methods.
AI also dramatically reduces false positives. Instead of drowning your security team in alerts, AI filters the noise and highlights genuine threats, allowing your experts to focus on what matters.
When a real threat is detected, automated mitigation can kick in instantly. The system can isolate devices, block traffic, and start containment without waiting for human approval. According to SANS Institute research, 49% of organizations now use AI for automated incident response because every second counts during an attack.

Our Managed Services and Security solutions put these AI capabilities to work for your organization, ensuring you benefit from cutting-edge threat detection without needing an in-house AI team.
Predictive Analytics and Proactive Threat Management
AI also offers predictive threat intelligence, analyzing historical data to forecast where future attacks are likely to originate. This changes vulnerability prioritization. AI helps identify which vulnerabilities are most likely to be exploited in your environment by considering factors like public exploit code and whether the system is internet-facing. This allows for smarter patching.
Attack vector forecasting takes this a step further, predicting how attackers might target your industry. This insight allows us to strengthen defenses in the most likely attack paths before criminals even make a move.
The result is smarter resource allocation. Your security budget and team’s time are focused on the threats that matter most. It’s like having a weather forecast for cyber threats—you can prepare for the storm before it hits.
This proactive approach is fundamental to effective Data Protection Strategies, ensuring your most valuable information stays secure.
Streamlining Attack Path Analysis and Incident Response
AI compresses weeks of manual attack path analysis into real-time, actionable insights. Exposure management powered by AI continuously monitors your attack surface, mapping how new vulnerabilities connect to critical assets.
During an incident, AI-driven automation transforms the response. It can immediately isolate systems, block traffic, and collect evidence, which can mean the difference between a minor incident and a major breach. Organizations using AI for incident response typically see response times cut by 50% or more.
Incident response planning also gets smarter. AI analyzes your environment to create customized response playbooks based on your actual systems and risk profile. Forensic analysis also benefits, as AI can automatically correlate events, identify the attack timeline, and suggest insights from past incidents.
For comprehensive preparedness, our Disaster Recovery & Backup solutions ensure you’re ready for what’s next, with AI-improved planning built-in.
The Rise of Generative AI in Cybersecurity Consulting
Generative AI is an exciting development in how cybersecurity consultants use AI. While known for content creation, its cybersecurity applications are profound. The technology’s ability to generate new, realistic data opens up previously unimaginable possibilities.
Security leaders are taking notice, with 67% showing interest in using GenAI to improve preventive cybersecurity practices. This isn’t just about automation; it’s about creating entirely new ways to protect organizations. GenAI is particularly valuable for creating custom solutions for each client’s unique environment, moving beyond one-size-fits-all approaches.
Practical applications of how cybersecurity consultants use AI for client solutions
Custom phishing training is one of the most effective applications. Instead of generic simulations, GenAI creates personalized fake emails that mirror actual communication styles. Companies using these tests have seen a remarkable 60% drop in click-through rates on malicious emails.
Automated security questionnaires transform administrative tasks. GenAI autofills assessments and compliance documents, saving up to 80% of the time spent on paperwork. This allows our consultants to focus on strategic threat analysis.
Threat summary generation is ideal for executive communication. GenAI distills complex reports into clear, actionable insights for the C-suite, translating technical findings into business-focused recommendations.
Beyond reporting, GenAI excels at code analysis. It can review application code, suggest security improvements, and generate test cases to validate fixes, dramatically speeding up secure development cycles. The technology also streamlines compliance automation by generating documentation and reports required by regulatory frameworks.

These applications show how cybersecurity consultants use AI for intelligence and efficiency that transforms the consulting relationship. Ready to see how generative AI can revolutionize your security strategy? Explore our comprehensive AI Solutions to find what’s possible for your organization.
Benefits, Challenges, and the Future of AI in Cybersecurity
The partnership between AI and cybersecurity consulting delivers remarkable results, but it comes with its own set of challenges. Understanding both sides helps organizations make informed decisions about their security investments.
The Primary Benefits of AI-Powered Consulting
Integrating AI into your security strategy brings immediate and lasting improvements. The primary benefit is increased efficiency, as AI automates repetitive tasks. For example, GenAI can save up to 20-25% of time in SecOps threat detection.
Reduced response times are another critical benefit. AI’s ability to detect and respond at machine speed shrinks both Mean Time To Detect (MTTD) and Mean Time To Respond (MTTR). Organizations with effective AI have detection and response times over 50% quicker than others.
Cost savings come from preventing breaches and streamlining processes. Improved accuracy results from AI’s ability to process vast datasets, find subtle patterns, and reduce false positives. Finally, AI provides 24/7 monitoring, with systems that automatically respond to threats around the clock, reducing the window of opportunity for attackers.
Our clients consistently experience these benefits, leading to faster threat containment, reduced analyst burnout, and a better compliance posture. Curious about the potential ROI? Our AI Impact Calculator can provide personalized insights.
Addressing the Challenges and Limitations of how cybersecurity consultants use AI
While promising, AI has challenges. Adversarial AI is a major concern, as malicious actors use it to create sophisticated attacks. For instance, phishing attacks have risen by 1,265% since GenAI became widespread. This creates an arms race requiring constant innovation.
Data poisoning (malicious training data) and model explainability (the “black box” problem) are key technical challenges. Poor data can compromise AI effectiveness, while a lack of transparency can hinder auditing.
The skills gap is also significant. There’s a high demand for workers trained in cloud security, AI, and zero-trust. This is where expert cybersecurity consultants become invaluable partners.
Implementation costs can be substantial upfront, though they lead to long-term savings. Most importantly, human oversight remains essential. AI augments human teams, not replaces them, and still requires human judgment for strategic decisions.
Continuous model training and establishing ethical guidelines are other key challenges to address. Learn more about our approach at AI Performance Optimization.
Future Trends: What’s Next for AI and Security?
The future of AI in cybersecurity is evolving rapidly. Hyperautomation will enable AI to handle more complex workflows, creating self-healing security systems with minimal human intervention.
Securing AI systems themselves is a critical new focus. Protecting AI models from attacks like data poisoning is a growing market, projected to reach $255 million by 2027 with a total addressable market of $10-15 billion.
Quantum security preparation is also underway. AI will be crucial in developing quantum-resistant cryptography to counter future threats from quantum computing. Most industries expect quantum security to be part of their cyber budget within five years.
AI will also strengthen Zero-Trust Architecture by enabling continuous, dynamic verification of users and devices based on behavior and context.
We continuously explore these developments to ensure our clients are equipped with future-proof technology. Read more about this commitment at Future-Proof Technology.
Frequently Asked Questions about AI in Cybersecurity Consulting
When businesses consider integrating AI into their security strategy, they have questions. Let’s address the most common concerns about how cybersecurity consultants use AI.
What specific AI technologies are most valuable for cybersecurity consulting?
Consultants leverage a suite of AI-powered tools. The most valuable include:
- Security Information and Event Management (SIEM): Uses machine learning to correlate and analyze security events.
- Security Orchestration, Automation, and Response (SOAR): Automates incident response workflows, taking action like isolating systems or blocking traffic automatically.
- Endpoint Detection and Response (EDR) & Network Detection and Response (NDR): Use AI to monitor behavior patterns on devices and across the network, spotting signs of compromise.
- User and Entity Behavior Analytics (UEBA): Establishes baseline behaviors for users and devices to immediately flag unusual activity.
These technologies form the backbone of a modern, intelligent security operation, working together like a digital security team that never sleeps.
Is AI replacing cybersecurity professionals?
No, AI is augmenting cybersecurity professionals, not replacing them. It’s making them more effective.
AI handles massive-scale data analysis and automates repetitive tasks, processing millions of events where a human can only handle hundreds. This frees human experts to focus on high-level strategy, complex threat hunting, and investigations that require critical thinking.
The role is evolving from a manual operator to an AI-system manager or “fine-tuner.” This evolution is liberating, allowing professionals to focus on challenging, strategic work instead of routine tasks and alert fatigue.
How can a small business start using AI for security?
AI-powered security is accessible to small businesses. The most practical way to start is by partnering with a managed IT and security services provider like us.
This approach provides access to enterprise-grade AI tools and expert management without the prohibitive upfront cost or need to hire specialized staff. You get the benefits of advanced AI security without having to become AI experts.
We typically recommend starting with foundational solutions like AI-enabled endpoint protection and AI-powered threat monitoring. This approach scales with your business, allowing you to layer in more sophisticated capabilities as you grow, building a security foundation for the future.
Conclusion: Your Partner in an AI-Secured Future
The change is complete. How cybersecurity consultants use AI has evolved from an experiment to an essential business strategy. What once seemed like science fiction is now the foundation of modern defense.
We’ve moved beyond traditional, reactive security. Today, AI enables us to predict threats, respond in milliseconds, and provide 24/7 protection that never gets overwhelmed. For consultants, AI is a trusted partner that amplifies our expertise. By automating detection, predicting threats, and streamlining responses, AI empowers businesses to stay ahead of adversaries.
Businesses we serve want partners who can prevent problems, not just fix them. That’s what AI-powered cybersecurity consulting delivers.
At Sundance Networks, we’ve witnessed how this technology transforms security from a necessary expense into a competitive advantage. We help businesses in Santa Fe, NM; Stroudsburg, PA; Reading, PA; Allentown, PA; Albuquerque, NM; and Rio Rancho, NM steer this new landscape with confidence. Our approach integrates intelligent AI solutions to build a robust and future-proof security posture, allowing you to focus on growing your business.
The future of cybersecurity is here, and it’s powered by AI. The question isn’t whether you’ll adopt these technologies, but how quickly and effectively you can implement them.
Ready to see how AI can transform your security strategy? Explore our AI Solutions or schedule a custom consultation today. Let’s build your AI-secured future together.
Contact Sundance Networks: (800) 944-2734 or visit our contact page.





