Why Managing Your IT Assets Is More Critical Than Ever
The IT asset management lifecycle is the structured process of managing your organization’s technology assets from initial planning and procurement through active use to secure disposal. It encompasses every stage an IT asset experiences during its useful life within your business.
Quick Answer: The IT Asset Management Lifecycle Stages
- Planning & Budgeting – Assess needs and allocate resources
- Procurement & Acquisition – Source and purchase assets
- Deployment & Integration – Install and configure for use
- Maintenance & Optimization – Monitor, maintain, and upgrade
- Retirement & Disposal – Securely decommission and dispose
Your business relies on dozens, hundreds, or even thousands of IT assets. From laptops and servers to software licenses and cloud subscriptions, these assets power your operations. But here’s the reality: 43% of enterprises still track their IT assets in spreadsheets while 56% don’t manage their IT assets lifecycle at all.
This approach creates serious problems. Without proper lifecycle management, you’re flying blind on critical business decisions. You might be paying for software nobody uses, running security risks on outdated hardware, or scrambling when critical systems fail unexpectedly.
The stakes are higher than ever. Modern businesses depend entirely on technology to serve customers, process payments, and store sensitive data. When your IT assets aren’t properly managed throughout their lifecycle, you face cascading risks – from security breaches to compliance violations to operational downtime.
The good news? A well-managed IT asset lifecycle transforms these challenges into competitive advantages. You’ll reduce costs, strengthen security, and gain the visibility needed to make smart technology investments.
What is IT Asset Management (ITAM) and Why is it Crucial?
Think of IT Asset Management (ITAM) as the complete care and feeding of every piece of technology in your business. It’s the systematic approach to tracking, managing, and optimizing all your IT assets from the moment you first consider buying them until you safely dispose of them years later.
ITAM covers everything that powers your business operations. This includes the obvious stuff like laptops, servers, and network equipment. But it also encompasses software licenses, cloud subscriptions, mobile devices, and even the valuable data your organization depends on. Basically, if it’s technology-related and has value to your business, it falls under ITAM.
The real power of ITAM lies in understanding Total Cost of Ownership (TCO). This means looking beyond that initial price tag to consider every dollar you’ll spend on an asset throughout its entire life. Maintenance contracts, software updates, energy costs, staff training, and eventual disposal all add up. When you understand the true TCO, you can make smarter purchasing decisions and squeeze more value from every technology investment.
Here’s what makes ITAM truly crucial: it transforms technology management from a reactive scramble into strategic business alignment. Instead of constantly putting out fires, you’re making data-driven decisions that support your company’s goals. Increasing operational efficiency was the top priority for organizations in 2022 (51%), and effective ITAM is your roadmap to getting there.
The Core Concept: The IT Asset Lifecycle
Every IT asset in your organization has a story – and that story has a beginning, middle, and end. The IT asset management lifecycle captures this entire journey, recognizing that every piece of technology has a finite lifespan where it can deliver value to your business.
This isn’t just about tracking when you bought something and when you threw it away. The lifecycle approach means actively managing each asset through distinct phases, from initial planning and procurement through daily operations to eventual retirement. Each stage presents opportunities to maximize value and minimize risks.
The magic happens when you shift from reactive to proactive management. Instead of waiting for servers to crash or software licenses to expire unexpectedly, you’re anticipating needs, scheduling maintenance, and planning replacements well in advance. This proactive approach keeps your operations running smoothly while avoiding those expensive emergency purchases and crisis situations that nobody enjoys.
The High Cost of Neglect
Ignoring proper IT asset management lifecycle practices is like never changing the oil in your car – things might run fine for a while, but eventually, you’re looking at a much bigger and more expensive problem.
Security vulnerabilities top the list of concerns. When you don’t know what assets you have or how they’re configured, you can’t protect them properly. Outdated systems with missing security patches become easy targets for cybercriminals. The stakes are real: the global cost of data breaches reached a record high of $4.88 million in 2024.
Wasted spending follows close behind. Without proper tracking, organizations routinely pay for software licenses they don’t use, buy duplicate hardware they already own, or maintain support contracts for equipment that’s been sitting in a closet for years. These “ghost assets” drain budgets while delivering zero value.
Compliance penalties can blindside unprepared organizations. Software audits, data protection regulations, and industry standards all require detailed asset records. When auditors come knocking and you can’t produce accurate documentation, the fines can be substantial. Plus, improper disposal of equipment containing sensitive data can trigger serious regulatory violations.
The inefficient operations that result from poor asset management create a ripple effect throughout your organization. Staff waste time hunting for equipment, IT teams can’t plan effectively, and leadership lacks the visibility needed to make informed technology investments.
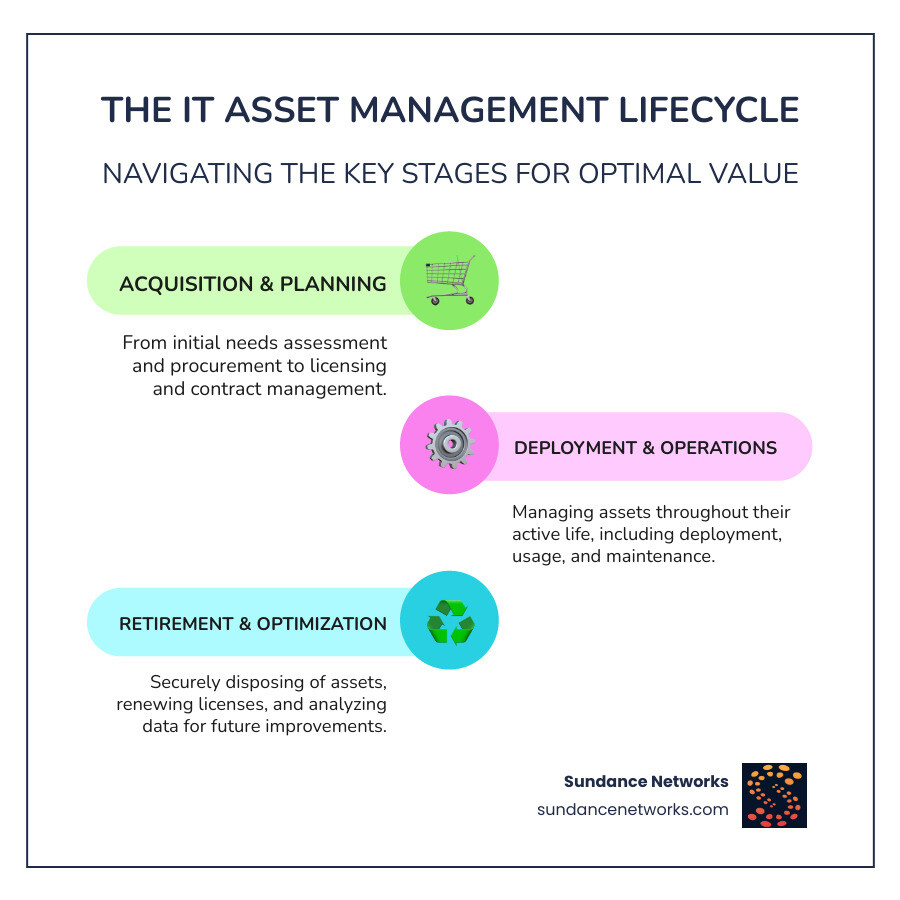
The 5 Key Stages of the IT Asset Management Lifecycle
Think of the IT asset management lifecycle as a roadmap that guides every piece of technology through your organization. While different companies might use slightly different terms or break things down into more steps, the core journey remains the same. Most successful organizations follow established frameworks like ITIL (Information Technology Infrastructure Library) and standards such as ISO 19770-1, which provide proven guidance for managing IT assets effectively.
We’ve found that breaking this process into five clear stages gives you comprehensive coverage from the moment you first think about acquiring an asset to the day you securely dispose of it. Each stage builds on the previous one, creating a seamless flow that maximizes value and minimizes risk.
Stage 1: Planning & Budgeting
Every great IT investment starts with a simple question: “What do we actually need?” This first stage is where smart organizations separate themselves from those who end up with expensive technology graveyards.
The planning process begins with a thorough needs assessment. You’ll work with teams across your organization to understand current gaps and future requirements. Maybe your sales team needs better laptops for client presentations, or your developers are struggling with slow servers. This collaborative approach ensures you’re solving real problems, not just buying the latest gadgets.
Forecasting future requirements is equally important. Technology moves fast, and what works today might be outdated in two years. You’ll want to consider how your business is growing, what new technologies are emerging, and how your current systems will scale.
Here’s where many organizations miss a golden opportunity: evaluating existing assets. Before you buy anything new, ask yourself if current equipment can be repurposed, upgraded, or simply moved to where it’s needed most. This single step can save thousands of dollars and reduce waste.
Budget creation during this phase goes far beyond the sticker price. You’ll calculate the Total Cost of Ownership (TCO), which includes maintenance, support, training, and eventual disposal costs. Smart planners also calculate the expected Return on Investment (ROI) to ensure every purchase delivers measurable business value.
Getting this stage right prevents the headaches that come later – overspending, compliance issues, and the dreaded “Why did we buy this?” conversations.
Stage 2: Procurement & Acquisition
Now comes the fun part – actually acquiring your assets. But before you get excited about shiny new equipment, this stage requires careful vendor evaluation. You’ll compare not just prices, but warranties, service level agreements, and long-term support options.
Contract negotiation is where preparation pays off. Armed with your planning research, you can secure better terms, favorable payment schedules, and service agreements that actually protect your interests. Don’t be afraid to ask for what you need – vendors want your business.
One crucial decision you’ll face is leasing versus buying. Purchasing gives you full ownership and potential tax benefits, while leasing offers flexibility and often lower upfront costs. Consider your cash flow, how quickly the technology might become obsolete, and your organization’s growth plans.
Standardization policies might sound boring, but they’re incredibly valuable. When you standardize on specific brands or models, you get better pricing through volume discounts, simplified maintenance, and easier staff training. Your IT team will thank you when they don’t have to support fifteen different laptop models.
For organizations looking to build robust infrastructure, our Hardware procurement expertise can help you steer these decisions with confidence.
Stage 3: Deployment & Integration
This is where your carefully planned assets come to life in your business environment. Asset tagging might seem like a small detail, but it’s absolutely critical. Each asset gets a unique identifier and detailed entry in your central inventory system. Think of it as giving each piece of equipment a birth certificate that follows it throughout its life.
Configuration and software installation transforms generic hardware into business tools. For employee devices, this means installing your standard software suite, security tools, and connecting to your network. For servers or specialized equipment, it involves complex integration with existing systems.
User assignment creates accountability. When someone receives a laptop or phone, they become responsible for its care and proper use. Clear policies at this stage prevent confusion and protect your assets.
The magic happens during integration with existing systems. Modern businesses use automated deployment tools and continuous integration pipelines to ensure new assets work seamlessly with current infrastructure. Everything gets updated in your digital asset register, creating a real-time view of your IT environment.
Whether you’re deploying in your own facility or the cloud, the principles remain the same. Learn more about our approach to On-Premise or Cloud deployment strategies.
Stage 4: Maintenance & Optimization
Welcome to the longest stage of the lifecycle – and arguably the most important. This is where proactive organizations shine and reactive ones struggle.
Proactive monitoring means watching performance metrics like speed, memory usage, and error rates before problems become crises. Modern monitoring tools can alert you to issues that users haven’t even noticed yet, giving you time to fix problems during maintenance windows instead of during the Monday morning rush.

Scheduled maintenance includes applying software patches, installing updates, and physically inspecting hardware for wear and tear. This preventive approach is crucial because over 80% of companies experience unplanned downtime, and the costs can be staggering. A few hours of planned maintenance can prevent days of unexpected outages.
Tracking usage and performance reveals surprising insights. You might find that expensive software licenses are barely used, or that certain hardware is being pushed beyond its limits. This data drives smart decisions about renewals, upgrades, and resource allocation.
Upgrades and renewals require careful cost-benefit analysis. Sometimes a simple memory upgrade extends a server’s life by years. Other times, the maintenance costs exceed the value of replacement. Smart organizations track these metrics to make informed decisions.
Protecting your operations from unexpected disruptions is essential. Explore our Disaster Recovery Backup solutions to ensure business continuity.
Stage 5: Retirement & Secure Disposal
The final stage is often overlooked, but it’s absolutely critical for security and compliance. Assets reach end-of-life for various reasons – they’re too old, broken beyond repair, or simply no longer meet business needs.
Decommissioning involves formally removing assets from active service and disconnecting them from your network. This prevents orphaned devices from becoming security vulnerabilities.
Data sanitization is non-negotiable. Before any device leaves your control, all data must be completely wiped using certified tools or physical destruction. This isn’t just about deleting files – modern data recovery techniques can retrieve “deleted” information from improperly wiped drives. The stakes are high, and cutting corners here can lead to devastating data breaches.
E-waste regulations vary by location, but they’re getting stricter everywhere. You can’t just throw old computers in the dumpster. Proper disposal protects the environment and keeps you compliant with local laws.
Value recovery opportunities include reselling functional equipment, donating to schools or nonprofits, or recycling components responsibly. Many organizations are surprised to find they can recoup significant value from assets they thought were worthless.
This stage ensures you maintain security, stay compliant, and minimize environmental impact. It’s the responsible way to complete the asset lifecycle.
For comprehensive protection throughout your IT assets’ entire lifecycle, robust cybersecurity is essential. Find our Cyber Security solutions.
Key Benefits of a Robust ITAM Strategy
Implementing a robust IT asset management lifecycle strategy transforms how your organization handles technology investments. It’s not just about tracking equipment – it’s about creating a strategic advantage that touches every corner of your business.
When you properly manage your IT assets through their complete lifecycle, you’ll see immediate improvements in several key areas.
- Cost savings become visible almost immediately as you eliminate waste and optimize spending.
- Risk mitigation strengthens your security posture and keeps you compliant with regulations.
- Improved efficiency streamlines operations and makes your team more productive.
Your security posture gets stronger when you know exactly what you have and how it’s protected. Regulatory compliance becomes manageable instead of stressful. And better forecasting helps you plan smarter investments for the future.
The beauty of effective ITAM is how these benefits compound over time. Each improvement supports the others, creating a positive cycle that makes your entire IT operation more reliable and cost-effective.
Optimizing Costs and Maximizing ROI
Here’s where ITAM really shines – in your budget. When you track every asset properly, you’ll be amazed at how much money you’re currently leaving on the table. Those ghost assets we mentioned earlier? They’re costing you real money every month. Software licenses for programs nobody uses, maintenance contracts on equipment that’s been sitting in storage, cloud subscriptions that were set up for a project that ended months ago.
Businesses with software license tracking experienced 12% less waste compared to those using basic tracking methods. That might not sound like much, but for most organizations, that translates to thousands or even tens of thousands of dollars annually.
The IT asset management lifecycle approach also gives you serious negotiating power with vendors. When you know exactly what you have, what you need, and when you need it, you can negotiate from a position of strength. Vendors respect organizations that come to the table with accurate data and clear requirements.
Smart maintenance scheduling extends your assets’ useful life too. Instead of running equipment until it breaks, you can plan upgrades and replacements strategically. This prevents those emergency purchases that always seem to happen at the worst possible time and cost twice what they should.
Strengthening Security and Ensuring Compliance
Not knowing what’s on your network is like leaving your front door wide open. A comprehensive IT management strategy closes those security gaps by giving you complete visibility into every device, every piece of software, and every access point.
When you know exactly what assets you have, you can ensure they’re all properly patched and configured. Those forgotten servers running outdated software? They become obvious targets for remediation instead of hidden vulnerabilities waiting to be exploited.
Compliance becomes much less stressful when you have accurate, up-to-date asset records. Whether you’re preparing for a software audit, demonstrating GDPR compliance, or meeting industry-specific regulations, having detailed documentation makes the process straightforward instead of panic-inducing.
The secure disposal component is particularly critical. When assets reach end-of-life, proper data sanitization protects your organization from data breaches that could happen long after you’ve forgotten about that old laptop or server. It’s not just about compliance – it’s about protecting your reputation and your customers’ trust.
To proactively identify and address potential vulnerabilities in your IT environment, consider our comprehensive Cybersecurity Scan.
Best Practices for a Successful IT Asset Management Lifecycle
Getting the IT asset management lifecycle right isn’t just about having good intentions—it requires a thoughtful, systematic approach that brings your entire organization together. Think of it like orchestrating a symphony: every instrument (department) needs to play in harmony, following the same sheet music (processes) to create something beautiful.
The foundation starts with a centralized asset inventory that serves as your single source of truth. No more hunting through different spreadsheets or wondering if the server list in Finance matches what IT actually has deployed. When everyone looks at the same data, you eliminate confusion and make smarter decisions.
Automation tools become your best friend here, handling the tedious tracking work so your team can focus on strategic initiatives. Cross-departmental collaboration between IT, Finance, and HR ensures that asset decisions align with business needs and budget realities. Regular audits keep everything honest and up-to-date, while ongoing employee training ensures everyone understands their role in the process.
Following established standards like ISO 55000 provides a proven roadmap that countless organizations have used successfully. These frameworks aren’t just bureaucratic paperwork—they’re battle-tested approaches that help you avoid common pitfalls.
Adopting the Right Tools and Technology
Let’s be honest: trying to manage today’s IT asset management lifecycle with spreadsheets and manual processes is like trying to steer a modern city with a hand-drawn map from 1995. It might work for a while, but you’re going to get lost, frustrated, and waste a lot of time.
Dedicated ITAM software transforms this challenge by providing a centralized platform where you can track, monitor, and report on every asset throughout its journey. These solutions often include automated findy capabilities that scan your network and identify hardware, software, and even cloud instances without you having to manually hunt them down.
Barcode and RFID scanners take the guesswork out of physical inventory management. Instead of relying on someone to remember where they put that laptop, you can scan and instantly know its location, condition, and assignment status.
The real magic happens when your ITAM solution integrates seamlessly with your IT Service Management (ITSM) platforms. Suddenly, when a user reports an issue, you can immediately see the asset’s history, warranty status, and configuration details. This integration connects the dots between asset data and service operations, making your entire IT team more effective.
For organizations with unique requirements or complex existing systems, custom solutions often provide the best fit. Our expertise in Custom IT Consulting and System Integration helps bridge the gap between your current processes and your ITAM goals.
Creating a Formal IT Policy
A well-crafted policy is like having a GPS for your entire asset management journey. Without it, different departments might take different routes to the same destination, creating confusion and inefficiency along the way.
Your policy should clearly define what you’re trying to achieve and which assets fall under its scope. Are you managing just computers and servers, or does it include software licenses, mobile devices, and cloud subscriptions too? Getting specific prevents gaps and overlaps that can cause problems later.
Defining roles and responsibilities eliminates the “I thought someone else was handling that” problem. When IT knows they’re responsible for technical configuration, Finance handles budgeting and contracts, and HR manages user assignments, everyone can focus on their strengths without stepping on each other’s toes.
The policy needs to establish clear procedures for each stage of the lifecycle, from initial planning through secure disposal. This isn’t about creating bureaucracy—it’s about ensuring consistency so that assets are handled the same way regardless of who’s managing them or when they’re being processed.
Security and compliance standards deserve special attention in your policy. With data breaches costing millions and regulations becoming stricter, your policy should specify exactly how sensitive data will be protected throughout an asset’s life and completely sanitized during disposal.
Finally, your policy should outline documentation requirements that create an audit trail without drowning your team in paperwork. The goal is having enough information to make good decisions and prove compliance, not creating a filing cabinet that nobody ever uses.
A good policy isn’t carved in stone—it should be reviewed and updated regularly as your technology, business needs, and regulatory environment evolve.
Future-Proofing Your Operations
The IT asset management lifecycle isn’t just another business process to check off your list. It’s the foundation that keeps your technology investments working for you, not against you. When you take control of every stage – from that first planning meeting to the final secure wipe of a retired server – you’re building something powerful: a technology environment that actually supports your business goals.
Think about it this way: every laptop, every software license, every cloud subscription has a story. The question is whether you’re writing that story or letting it write itself. With proper lifecycle management, you become the author. You decide when assets come in, how they’re used, and when they gracefully exit. Without it, you’re stuck reacting to whatever plot twists come your way.
Proactive management transforms challenges into competitive advantages. While your competitors scramble to find budget for unexpected replacements or deal with security breaches from forgotten assets, you’re making strategic decisions based on real data. You know exactly what you have, what it costs, and when it needs attention.
At Sundance Networks, we’ve helped businesses transform their IT chaos into organized, efficient operations. We know that behind every asset tag and inventory number is a real business need. Whether you’re a growing company in Stroudsburg or an established organization expanding into new markets, we bring the same commitment to making technology simple and secure.
Your IT environment doesn’t have to be a source of stress. With the right approach to asset lifecycle management, it becomes a strategic advantage that grows with your business. Every properly managed asset contributes to your success story, from improved security to better budget control to smoother daily operations.
Ready to turn your IT challenges into opportunities? Take control of your IT environment with our Managed Services and Security. Let’s build something great together.